This section makes frequent use of data contained in the Technical Requirements.
All relevant sections of the Technical Requirements Data collection should be completed or known before commencing with the steps in this section.
Create CUBE User
VSM requires the user to be created on any Cisco IOS device. The user is required to run show commands.
User can be created using one of two options.
TACACS Option
If the client is using TACACS or Radius to control IOS users, ask the client to create an account that can access the CUBE with level 5 privileges.
Confirm with the TACACS team that you can run 'show' commands with the created account.
Test the account by logging into the CUBE (SSH to CUBE with the created account) and run ALL the commands shown below.
Make sure each command displays some output after being run.
Router# show running-config Router# show startup-config Router# show platform software mount Router# show platform software Router# show platform Router# show dial-peer voice summary Router# show dial-peer voice Router# show dial-peer Router# show call active voice compact Router# show users Router# show Router# show environment
Local User Option
Login to IOS and enter the following commands:
Router(config)# username {Enter User Here} privilege 5 Password {Type Password}
Router(config)# privilege exec level 5 show platform software mount
Router(config)# privilege exec level 5 show platform software
Router(config)# privilege exec level 5 show platform
Router(config)# privilege exec level 5 show dial-peer voice summary
Router(config)# privilege exec level 5 show dial-peer voice
Router(config)# privilege exec level 5 show dial-peer
Router(config)# privilege exec level 5 show
Test the account by logging to the CUBE (SSH to CUBE with the account created) and run ALL the commands shown below.
Make sure each command displays some output after being run.
Router# show running-config Router# show startup-config Router# show platform software mount Router# show platform software Router# show platform Router# show dial-peer voice summary Router# show dial-peer voice Router# show dial-peer Router# show call active voice compact Router# show users Router# show Router# show environment
CUBE SNMP Configuration
SNMP Version 2 option
Configure the SNMP Community using the following commands:
Router(config)# snmp-server community {Enter SNMP Value here} RO
Router(Config)# snmp-server location <location> #This command is optional and may needed only if you want to specify the location.
Router(Config)# snmp-server contact <contact info> #This command is optional
Configure the VSM probe as the SNMP Host.
Router (Config)# snmp-server host {Enter VSM Probe IP Address here}
[traps | informs] version 2c community-string [udp-port port-number] [notification-type]
The following example demonstrates a sample configuration of SNMP Version 2.
Router(Config)# snmp-server community VirsaeVSM RO Router(Config)# snmp-server location BHIVE Auckland Router(Config)# snmp-server contact Virsae Support Team Router(Config)# snmp-server host 10.10.10.20 version 2c VirsaeVSM Router(Config)# snmp-server enable traps snmp authentication linkdown linkup coldstart Router(Config)# snmp-server enable traps cpu threshold Router(Config)# snmp-server enable traps ipsla Router(Config)# snmp-server enable traps config-copy Router(Config)# snmp-server enable traps license Router(Config)# snmp-server enable traps envmon Router(Config)# snmp-server enable traps bgp
SNMP Version 3 option
Router(config)# snmp-server view {Enter View Name Here}
Router(Config)# snmp-server group <Group Name> v3 [priv|auth|noauth] read <View Name >
Router(Config)# snmp-server user <username> <Group Name> v3 [encrypted] [auth {md5 | sha} auth-password]}
Router(Config)# snmp-server host <Enter VSM Probe IP Address here> version 3 [auth|no auth|priv] <Enter user name here>
The following demonstrates a sample configuration of SNMP Version 3 with Parameters shown in the following table
| Parameter | Value |
|---|---|
| View Name | virsaelab |
| Group Name | VSMMonitor |
| Username | VSMUser |
| Auth Password | P@ssword123 |
Router(Config)# snmp-server view virsaelab iso included Router(Config)# snmp-server group VSMMonitor v3 priv read monitor Router(Config)# snmp-server user VSMUser VSMMonitor v3 auth sha P@ssword123 Router(Config)# snmp-server host 192.168.5.180 version 3 auth VSMUser Router(Config)# snmp-server enable traps snmp authentication linkdown linkup coldstart Router(Config)# snmp-server enable traps cpu threshold Router(Config)# snmp-server enable traps ipsla Router(Config)# snmp-server enable traps config-copy Router(Config)# snmp-server enable traps license Router(Config)# snmp-server enable traps envmon Router(Config)# snmp-server enable traps bgp
CUBE Syslog Configuration
Enter the IP Address of the VSM Probe as the destination for the log files.
Syslog files have logging based on the client's logging configuration.
Router(Config)# logging host (Enter VSM Prob IP Address) Router(Config)# logging traps (i.e 0 1 2 3 4 5 .. according to your requirement)
Web Portal Configuration
Add CUBE
Log in to the VSM web portal using your VSM credentials and password.
For your customer, select Service Desk > Equipment Locations. Right-click on the Equipment Location (Appliance) that will serve this particular UC Server and select ‘Manage Equipment’.
At the bottom of the ‘Manage Equipment’ page, click the ‘Add Equipment’ button.
A form will open which you can populate with the equipment details as per the table below.
Select the Vendor ‘Cisco Systems’ and Product ‘Unified Border Element’.
If you are adding more than one piece of the same equipment type, check the ‘Add another’ box at the bottom of the form and the bulk of the configuration will be carried over for the next item.
| Field | Setting |
|---|---|
Vendor | Cisco Systems |
Product | Unified Border Element |
Equipment Name | Friendly name for this CUBE |
Username | Administrative Username |
Password | Administrative Password |
IP Address / Host Name | IP Address of server (Virtual in duplicated servers) |
Site | Free text field, this information will be included in alarm notifications from the VSM Workflow. |
Site ID information in the ‘Site’ field will advise your NOC staff of the site where the Microsoft Server (i.e. the VSM Collector) is physically located.
This is particularly helpful when the customer has multiple sites.
SNMP
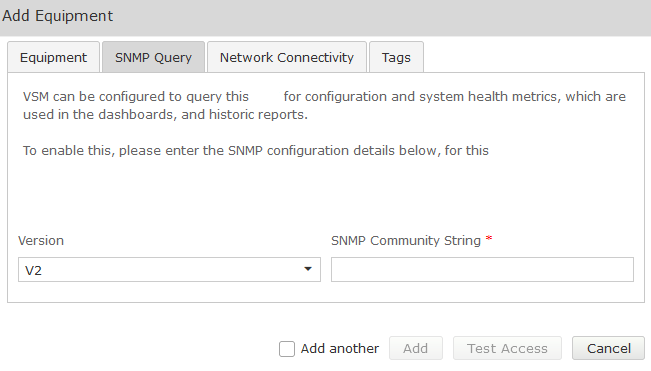
Complete the Equipment tab and then click on the ‘SNMP Query’ tab.
Click on the down arrow, and select the SNMP version you wish VSM to use for querying the CUBE:
SNMP V1 or V2
| Field | Setting |
|---|---|
Version | V1, V2 |
SNMP Community String | Community String as administered on the CUBE |
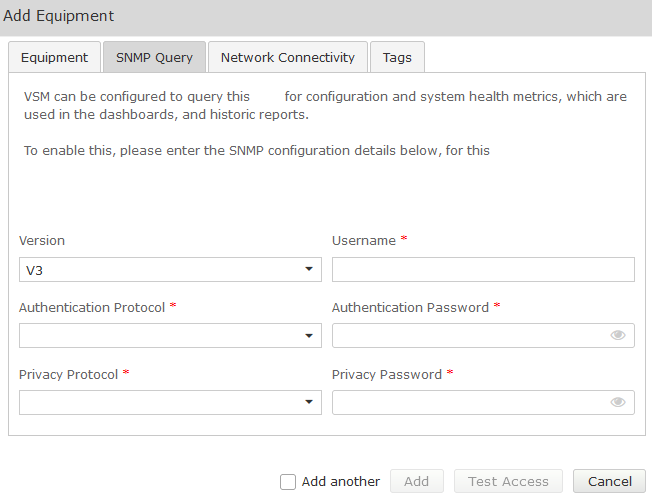
SNMP V3
| Fields | Setting |
|---|---|
Version | V3 |
Username | SNMP V3 Username (refer to technical requirements forms) |
Authentication Protocol | SHA (Recommended) |
Authentication Password | Password (refer to technical requirements) |
Privacy Protocol | DES (Recommended) |
Privacy Password | Password (refer to technical requirements forms) |
Test Access
Once all fields are populated Click on the Test Access button. This will test that VSM can connect to the CUBE using the settings you have entered:
Both SSH and SNMP should return success. If not, troubleshoot the configuration.
- The SSH test ensures the VSM probe can connect to, and log in using the account configured.
- The SNMP test ensures an SNMP query can be run.
Once testing is successful, click Add.