AXL Configuration
VSM use AXL API to collect data from CUCM, this can be achieved by creating user with AXL Capabilities within CUCM.
Enable AXL Service
Go to Cisco Unified Serviceability.
Logging to Serviceability
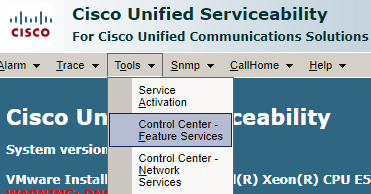
Go to Tools >>Control Centre - Feature Service.
Tools>>Feature service
Select server – Choose Publisher
Make Sure AXL Web Service status is started, otherwise start it if it was deactivated or stopped.
AXL Web Service status
Create CUCM AXL User
Log in to Cisco Unified CM Administration to create AXL user.
Log in to Cisco Unified CM Administration
Create Access control group with AXL privilege for AXL user.
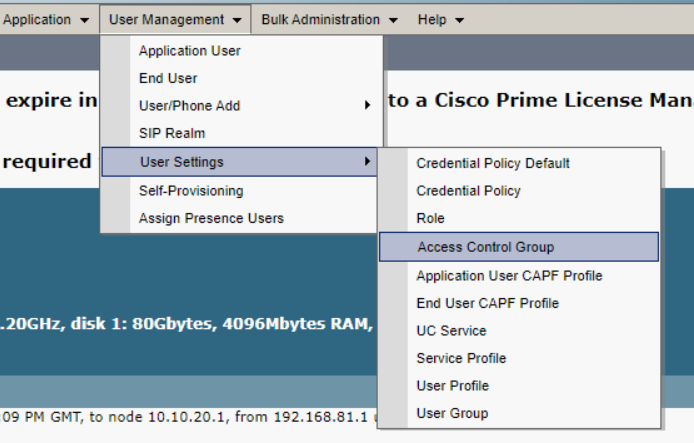
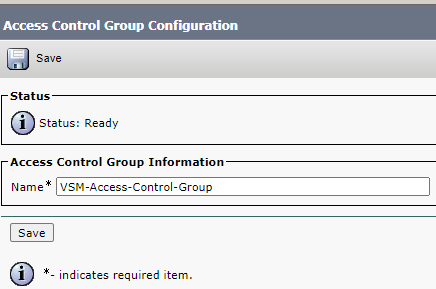
Go to User Management>>User Settings >>Access Control Group>>Add new
Access Control Group
Add New Access Control Group
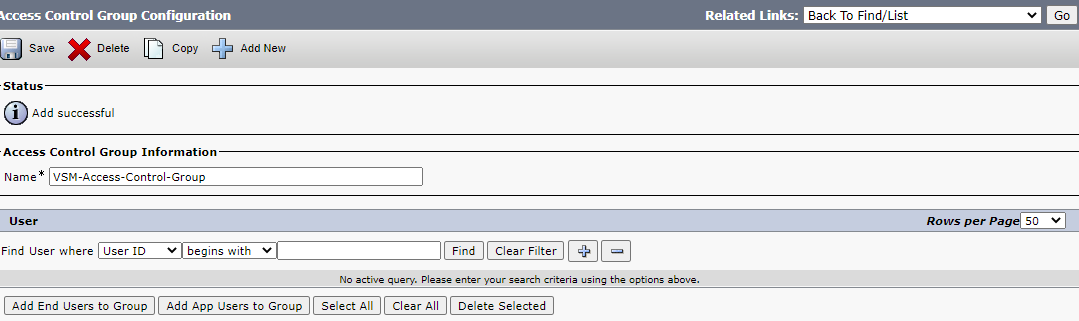
Enter the Access control group name and click save.
Create Access Control Group
On the related links on click Assign Role to Access Control Group
Access Control Group Related Links
Assign Role to Access Control Group
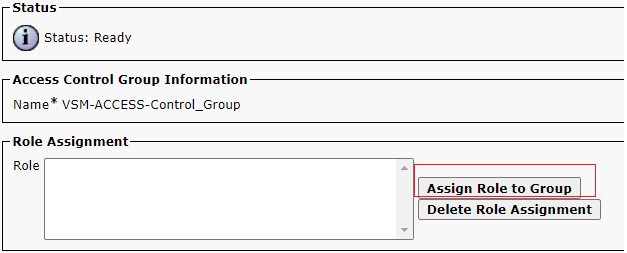
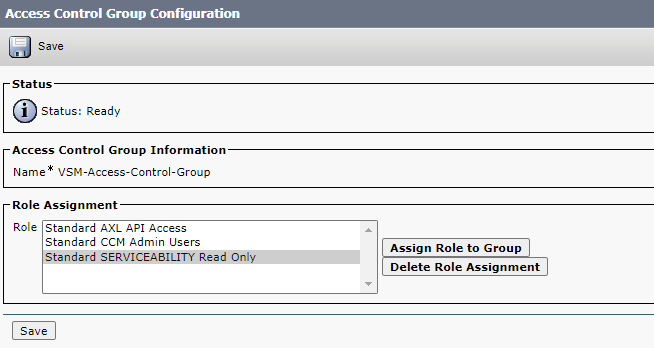
On the Access Control Group Information Click on Assign Role to Group.
Assign Role to Group
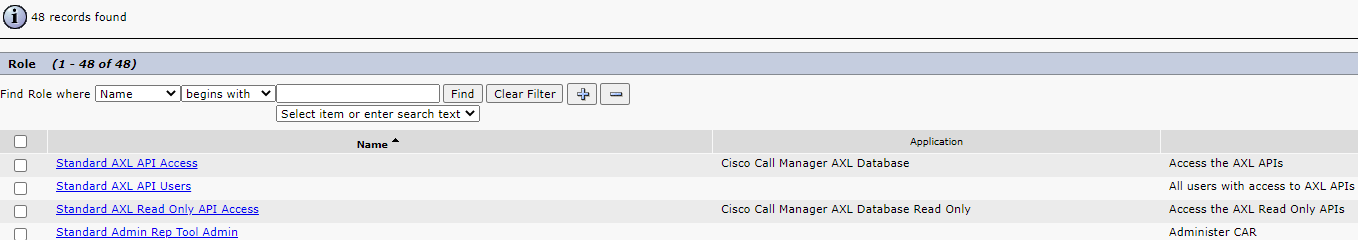
List of Roles of page appear with all the roles.
List of Roles
Select the checkbox for the following rules and click Add Selected:
- Standard AXL API Access.
- Standard CCM Admin Users.
- Standard SERVICEABILITY Read Only.
The following Page displays, click save.
Access Control Group with Roles assigned
Go to User Management>>Application User>>Click Add New
Application User Page
Enter user details in the Application User Information.
Application User Information
Field | Value |
User ID | This is the user that is going to be used by VSM to access the CUCM |
Password | Enter the password for the new user. |
Confirm Password | Type the same password again. |
Application User Information
Figure 16 – VSM Application User
- Under Permission Information in the new created Application User click on Add to Access Control Group.
Figure 17 – Application User Configuration – Permission Information
- In the search bar type the name of previously created Access Control Group.
Figure 18 – Find and List Access Control Groups
- Enter the name of previously created Access Control Group >>Click Find>>Check the checkbox next to Access control Group and Click Add Selected.
Figure 19 – Assign AXL Access Control Group to the VSM AXL User
- Click Save under Application User Configuration.
Figure 20 – Application user with the new Access Groups Assigned
- Once You click Save it will show the list of roles assigned to the user.
Figure 21 – Application User Final Status.
- Make sure you can sign in to CUCM with the newly created account by signing out and sign back in again with the your new account.
Figure 22 – Signing to CUCM with the new AXL Account
1.2. CUCM SNMP Configuration
SNMP configuration is required as part of CUCM Monitoring, SNMP can be configured as V1 ,V2 or V3 based on the customer requirements.
1.2.1. Configure SNMP V1/V2
- Navigate to Cisco Unified Serviceability>>SNMP>>V1/V2>>Community String
Figure 23 – Cisco Unified Serviceability Navigation
Figure 24 – SNMP V1/V2
Figure 25 – SNMP Community String Configuration
- From the drop down List Choose the server you want to configure SNMP and click find>>Add new if none was configured.
SNMP need to be configured on all the servers in CUCM Cluster.
Figure 26 – SNMP Community String Configuration
- Fill in the SNMP Community String Page with the following values.
Table 2 – SNMP Community String Configuration
Field | Value |
Community String Name | Enter the required Name |
Hosted IP Address Information | Choose one of the following based on the client requirements 1- Accept SNMP Packets from Any host. 2- Accept SNMP Packets only from these Hosts If you choose Accept SNMP Packets only form these hosts make sure to enter IP Address of VSM Probe server under Host IP Address |
Access Privilege | Choose ReadNotifyOnly unless something else required from the customer |
Apply to All Nodes | Check the check box to apply configuration to all servers within the cluster. |
Figure 27 – SNMP Community String Configuration
Figure 28 – SNMP Sample Configuration
- When you click save warning will display notifying of restarting SNMP Master Agent Service for the change to take effect, click ok to restart the service.
Figure 29 – SNMP Service Restart
- Once completed the following message display with the status of the restart.
Figure 30 – SNMP Service Restart Status
- Configure CUCM to send SNMP Traps by navigating to SNMP>>V1/V2>>Notification Destination
Table 3 – SNMP Notification Destination
Field | Value |
Host IP Address | VSM Probe IP Address |
Notification Type | Trap |
Figure 31 – SNMP Notification Destination
- Choose server >>Find>>Click Add New
Figure 32 – SNMP Notification Destination Server Selection
- The following page appear, from the drop down list choose Add new.
Figure 33 – SNMP Notification Destination Configuration
Figure 34 – SNMP Notification Destination Configuration Drop Down List
- Enter the Values in the page as per following
Table 4 – SNMP Notification Destination
Field | Value |
Host IP Addresses | Add New is selected |
Host IP Address | VSM Probe IP Address |
Port Number | Default is 162, change it only if needed |
SNMP Version | Choose either V1/V2C |
Notification Type Information | Trap |
Figure 35 – SNMP Notification Destination Configuration – Add New Page
Figure 36 – SNMP Notification Destination Configuration Sample Configuration
- Once you choose notification Type Community String Information will Display,choose the community String created earlier and check apply to All Nodes.
Figure 37 – SNMP Notification Destination Configuration – Apply To All Nodes
- Click ok for the pop to restart the SNMP Master Agent Service as before unless client want to do it later.
Figure 38 – Notification Destination Service Restart.
- Once restart is completed SNMP Notification Destination Configuration will show the new Destination IP Address.
Figure 39 – SNMP Notification Destination Configuration Status
1.2.2. CUCM SNMP V3 Configuration
- Navigate to Cisco Unified Serviceability>>SNMP>>V3>>SNMP Destination Configuration and follow the same steps described earlier to add SNMP V2 Destination
Figure 40 – SNMP V3 SNMP Destination Configuration
- Select Server from the drop down list and click find.
Figure 41 – SNMP V3 User Configuration
- Click Add New to create SNMP User
Table 5 – SNMP V3 User configuration
Field | Value |
User Name | Enter SNMP User Name |
Authentication Required | Check the checkbox of Authentication |
Password | Enter the Password |
Protocol | Choose either MD5 or SHA |
Privacy Required | Optional/check the checkbox if required |
Password | Enter the password |
Protocol | Choose the preferred Protocol (DES/AES128) |
Accept SNMP Packets from Anyhost | Uncheck the checkbox |
Accept SNMP Packets only from these Hosts | Check the Check box |
Host IP Address | Enter the IP Address of the VSM Probe and click Insert |
Access Privileges | Choose ReadNotify Only |
Apply to All Nodes | Check the checkbox |
Figure 42 – SNMP V3 User Configuration Page
Figure 43 – SNMP V3 User Configuration Example
- Click ok to the pop up to restart SNMP master agent for configuration to take effect
Figure 44 – SNMP Master Agent Pop UP to restart the service
- Once restart is completed SNMP user configuration will be displayed with the new user configured.
Figure 45 – SNMP V3 User Configuration
- Follow the same steps described in configuring SNMP Notification Configuration on SNMP V2 section.
Figure 46 – SNMP V3 Notification Configuration
1.3. CUCM syslog configuration
- Navigate to Cisco Unified CM Administration >> System >> Cisco Syslog Agent >>Remote Syslog Server Name
- Enter the IP Address of VSM Probe as one of Remote Syslog Severs.
- Syslog Severity for Remote Syslog messages >> Choose based on the requirements
Figure 47 – CUCM Syslog configuration
1.4. CDR Configuration
- Navigate to Cisco Unified Serviceability>>Tools >> Control Centre – Feature Service >>Select Publisher from the drop down list and make sure All CDR services are up.
Start the services if it was deactivated or stopped.
Figure 48 – Control Centre – Feature Service CDR Services
- Navigate to Cisco Unified Serviceability >> Tools >> Control Centre – Network Services >> Select Publisher from the drop down list and make sure all CDR services are up.
Figure 49 – Control Centre – Network Services Publisher CDR Services
- Navigate to Cisco Unified Serviceability >> Tools >> Control Centre – Network Services >> Select Subscriber from the drop down list and make sure CDR Agent service is running.
- Repeat the above step for all subscribers in the Cluster.
Figure 50 – Control Centre - Network Services Subscriber CDR Service
- Navigate to Cisco Unified CM Administration >> System >> Service Parameter >> Call Manager Service. Set the CDR Enabled Flag to True. This has to be done for all the nodes in the server.
Figure 51 – CUCM Service Parameters Configuration
Figure 52 – Set up CDR Enabled Flag and CDR Log Calls with Duration to True
- Repeat above step for all CUCM Servers in the cluster.
- navigate to System >> Service Parameter >> Call Manager Service>> Clusterwide Parameters >> Call Diagnostics Enabled parameter to Enabled Only When CDR Enabled Flag is True
Figure 53 – Setup Call Diagnostics – Enable CMR
- Now add SFTP server/Billing Server where the files are to be sent. Navigate to Cisco Unified Serviceability > Tools > CDR Management and add new billing server.
Figure 54 – CDR Management Page
Table 6 – Billing Application Server Parameters
Field | Value |
Host Name /IP Address | Enter Probe IP server |
Username | Enter username details for SFTP |
Password | Enter Password details for SFTP |
Protocol | SFTP |
Directory Path | \ |
Resend on Failure | Check the checkbox |
Figure 55 – Billing Application Server Parameters
1.5. CUCM Backup Configuration
The following is required to configure VSM as destination for backup files. These Backup files will be sent from the VSM Probe to the Virsae Cloud.
- Navigate Disaster Recovery System >> Backup >> Backup Device >> Add New
Figure 56 – Disaster Recovery Page
- Enter the required details for the Backup Device
Table 7 – Backup Device Details
Field | Value |
Backup Device Name | Enter Any name |
Host name / IP Address | VSM Probe IP Address |
Path name | \ |
User name | VSM SFTP server username |
Password | VSM SFTP server password |
Number of backups to store on Directory | Leave it to default – VSM Probe will send the backups to Virsae Cloud. |
- Configure backup scheduler by navigating to Backup >> Scheduler.
- Define Scheduler Name. Select the Device name (the device created earlier) and check the features you want to backup, ideally check all the options.
- If using CUCM prior to Version 12.0, the features are CDR_CAR, UCM and PLM. If using CUCM Version 12.0 and later, the features are CDR_CAR, UCM and IM_AND_PRESENCE.
Figure 57 –CUCM Backup features prior to Version 12.0
Figure 58 - CUCM Backup features for Version 12.0 and later
- Configure a schedule backup based on your scenario, recommended Daily backup after hours.
Figure 59 – Backup Schedule
- Click on Save and notice the warning as shown in the image. Click on OK in order to move forward.
Figure 60 – Backup Warning
- Once the Backup Schedule is created, click on Enable Schedule
Figure 61 – Enable Schedule
- Make sure the schedule status is changed to Enabled.
Figure 62 – Schedule Backup Enabled
1.6. Web Portal Configuration
1.6.1. Add CUCM
Login to the VSM web portal using your credentials and password.
For your customer, select Service Desk > Equipment Locations. Right-click on the Equipment Location (Appliance) that will serve this particular UC Server and select ‘Manage Equipment’
At the bottom of the ‘Manage Equipment’ page click on the ‘Add Equipment’ Button
A form will open which you can populate with the equipment details as per table 8.
Select the Vendor ‘Cisco Systems’ and Product ‘Unified Communications Manager’.
Figure 63 – Web Portal – Add Equipment
If you are adding more than one piece of the same equipment type check the ‘Add another’ box at the bottom of the form and the bulk of the configuration will be carried over for the next item.
Table 8 - Web Portal – Add CUCM Field Description
Field | Setting |
Vendor | Cisco Systems |
Product | Unified Communications Manager |
Equipment Name | Friendly name for this CUCM |
Username | Administrative Username |
Password | Administrative Password |
IP Address / Host Name | IP Address of server (Virtual in duplicated servers) |
Site | Free text field, this information will be included in alarm notifications from the VSM Workflow. |
Use Cisco APIs | Select if Using Cisco APIs for advanced options |
- Site ID information in the ‘Site’ field will advise your NOC staff of the site where the Microsoft Server is physically located. This is particularly helpful when the customer has multiple sites.
Figure 64 - Web Portal - CUCM Configure Equipment
Complete the Equipment tab and then click on the ‘SNMP Query’ tab.
Click on the down arrow, and select the SNMP version you wish VSM to use for querying the CUCM:
SNMP V1 or V2
Figure 65 - Web Portal – CUCM SNMP V1/V2 Query
Table 9 - CUCM SNMP V1/V2 Field Descriptions
Fields | Setting |
Version | V1, V2 |
SNMP Community String | Community String as administered on the CUCM |
SNMP V3
Figure 66 - Web Portal – CUCM SNMP V3 Query
Table 10 - CUCM SNMP V3 Field Description
Fields | Setting |
Version | V3 |
Username | SNMP V3 Username |
Authentication Protocol | SHA (recommended) |
Authentication Password | Password |
Privacy Protocol | DES (recommended) |
Privacy Password | Password |
Once all fields are populated Click on the Test Access button. This will test that VSM can connect to the CUCM using the settings you have entered:
Figure 67 - Web Portal – CUCM Test Access
Both SSH and SNMP should return success. If not, trouble-shoot the configuration.
- The SSH test ensures the VSM probe can connect to, and login using the account configured.
- The SNMP test ensures an SNMP query can be run.
Once testing is successful, click Add.