This section makes frequent use of data contained in the Technical Requirements.
All relevant sections of the Technical Requirements Data collection should be completed or known before commencing with the steps in this section.
There are two parts to the configuration, the first being the server(s) under management, and the second being the supporting configuration on the web portal.
Both are covered in this chapter.
ASM Configuration
Adding a new Session Manager Login
Create an Administrator account. The VSM Probe requires access with Administrative rights.
Add an account that, when used, provides access to the Linux bash prompt:
Start an SSH session. At the command prompt type:
$ su root
- When prompted enter the 'root' user password.
Use the command:
$ useradd {NAME}where NAME is the account name to create.
Use the command:
$ passwd {NAME}where NAME is the account name created above.
Hit enter. Enter the password then hit enter again.
You will now need to give this account 'custadmins' and 'suser' permissions. This will allow the new account to run the commands required to collect data. To do this enter the command:
- For versions below 10.2 use the following command:
$ usermod -G 1000,1005 {NAME}
- For versions 10.2 and above use the following command:
$ usermod -G 1000,1007 {NAME}
Enter the command:
$ chage –M 99999 {NAME}To set the System Manager account password to: "not expire".
- NAME is the account created above.
If you do not have root access, your Business Partner or Avaya may be able to create this account on your behalf, or you can use the ‘cust’ credentials instead.
Configure SM SNMP Traps
This section requires the Virsae SNMP Target Profile to be set up in System Manager. If this is not the case, please refer to the System Manager Configuration Page before proceeding.
In System Manager, navigate to Manage Serviceability Agents > Serviceability Agents:
Select an agent from the Agent List window, in this case, the Session Manager and click on the Manage Profiles button.
From the Manage Profiles window, under the SNMP Target Profiles tab, select the Virsae profile, click on 'Assign' and then the 'Commit' button.
Configure SIP Station SNMP Query
To enable VSM to understand the IP Endpoint configuration, the SIP stations must allow VSM to proactively run queries.
Make these changes in the 46xxSettings.txt files as follows. (refer to technical requirements forms):
In the SNMP section edit and uncomment the following settings:
SET SNMPADD {VSM Probe IP Address (V4)}
SET SNMPSTRING {SM SNMP Community Name}
Configure RTCP Monitoring and Endpoint SNMP Query
To allow VSM to monitor the voice quality of SIP endpoint calls and gather phone configuration data via SNMP, configure Session Manager to send RTCP reporting to the IP address of the VSM probe.
From the main 'System Manager' dashboard, navigate to Elements > Session Manager. Navigate to Device and Location Configuration > Device Settings Groups:
Click on the 'Default Group' button.
Expand ‘Maintenance Settings’. Add the IP address of the VSM Client in the ‘IP Address For SNMP Queries’ field and add the community string to the ‘SNMP Community’ field.
SM Device Maintenance Settings Default Group Field Description
| Fields | Setting |
|---|---|
IP Address For SNMP Queries | IP Address of the VSM probe |
SNMP Community | SNMP Community Name (refer to technical requirements forms) or use public |
All other items may be left as is.
Expand 'VoIP Monitoring Manager'. Add the IP address of the VSM Client, the port for the RTCP receiver you wish to send the RTCP data to (default is 5005), and the reporting period (default is 5 seconds).
SM Device Settings Default Group Field Description
Field | Setting |
|---|---|
IP Address | IP Address of the VSM probe |
Port | 5005 - *See Note |
Reporting Period | 5 |
Note: A single Equipment Location can support multiple RTCP Receivers.
Each individual ACM and its adjuncts should report to a separate discrete RTCP Receiver using a unique port for each.
Once complete click 'Save'.
Configure CDR and Syslog
From the main System Manager navigate to Elements > Session Manager> Session Manager Administration:
From the Session Manager Administration window (shown above) select the Session Manager Instances tab, select the Session Manager and click on Edit.
Scroll down to the CDR section and configure as per the table below.
SM CDR Field Description
Field | Setting |
|---|---|
Enable CDR | Checked |
Password | SFTP Password |
Data File Format | Standard Flat File |
Include User to User Calls | Unchecked |
Include Incomplete Calls | Unchecked |
Scroll down to the Logging section and configure as per the table below.
If no Syslog Servers are populated, check ‘Enable Syslog Server 1’ or ‘Enable Syslog Server 2’ and fill out the form fields.
If Syslog Server 1 is populated, check ‘Enable Syslog Server 2’ and fill out the form fields as per the table above.
Note: If both Syslog Servers are already populated you cannot administer Syslog at this time. Please contact Virsae for further assistance.
SM Logging Field Description
| Field | Setting |
|---|---|
Transport | UDP |
IP Address or FQDN | IP Address of VSM collector |
Port | 514 |
Click on the Commit button.
SIP Tracer
Session Manager Version6.x - Version7.x
Navigate to Elements > Session Manager > System Tools > SIP Tracer Configuration:
Select the Session Manager you wish to configure from the 'Session Manager Instances' list, then click the 'Read' button at the top of the page
Configure using the table below, then click the 'Commit' button at the top of the page. Repeat this for any other Session Managers you wish to administer for SIP Trace output.
SM SIP Tracer Field Description
Field | Setting |
|---|---|
Send Trace Method | Syslog |
Tracer Enabled | Checked |
Trace All Messages | Checked |
| From Network to Security Module | Unchecked or Grey |
| From Server to Security Module | Unchecked or Grey |
| Trace Dropped Messages | Unchecked or Grey |
| Send Trace to a Remote Server | Checked |
Remote Server FQDN or IP Address | IP Address of VSM collector |
| Stunnel Port | Grey (Not Required) |
| From Security Module to Network | Unchecked or Grey |
| From Security Module to Server | Unchecked or Grey |
| Max Dropped Message Count | 1 or higher |
| Send Trace Method | Syslog (Unsecure UDP) |
‘Max Dropped Message Count’ cannot be zero. Increase this to 1 at a minimum.
Session Manager Version8.x and Later
Select the Session Manager you wish to configure from the 'Session Manager Instances' list then click the 'View' button at the top of the page.
Configure as per the table below then click the ‘Commit’ button at the top of the page. Repeat this for any other Session Managers you wish to administer for SIP Trace output.
SM SIP Tracer Field Description
| Field | Setting |
|---|---|
Tracer Enabled | Checked |
Trace All Messages | Checked |
| From Network to Security Module | Unchecked or Grey |
| From Security Module to Network | Unchecked or Grey |
| From Server to Security Module | Unchecked or Grey |
| From Security Module to Server | Unchecked or Grey |
| Trace Dropped Messages | Unchecked or Grey |
| Max Dropped Message Count | 1 or higher |
‘Max Dropped Message Count’ cannot be zero. Increase this to 1 at a minimum.
Web Portal Configuration
Add SM
Log in to the VSM web portal using your credentials and password.
For the particular customer, select Service Desk > Equipment Locations. Right-click on the Equipment Location that will serve this particular SM and select ‘Manage Equipment’
At the bottom of the ‘Manage Equipment’ page click on the ‘Add Equipment’ button.
A form will open which you can populate with the equipment details.
Select the Vendor ‘Avaya’ and Product ‘Session Manager’.
If you are adding more than one piece of the same equipment type, check the ‘Add another’ box at the bottom of the form and the bulk of the configuration will be carried over for the next item.
Web Portal – Add SM Field Description
Field | Setting |
|---|---|
Vendor | Avaya |
Product | Session Manager |
Equipment Name | Friendly name for this SM |
Username | The administrative username you added to SM earlier |
Password | The administrative password you added to SM earlier |
IP Address / Host Name | IP Address of server |
Site | Friendly name for core site (where this server is located) |
SNMP
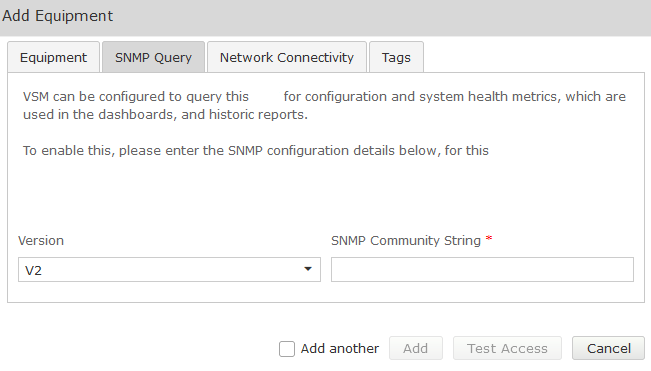
Complete the Equipment tab and then click on the ‘SNMP Query’ tab.
Click on the down arrow, and select the SNMP version you wish VSM to use for querying the equipment:
SNMP V1 or V2
| Field | Setting |
|---|---|
Version | V1, V2 |
SNMP Community String | Community String as administered on this equipment |
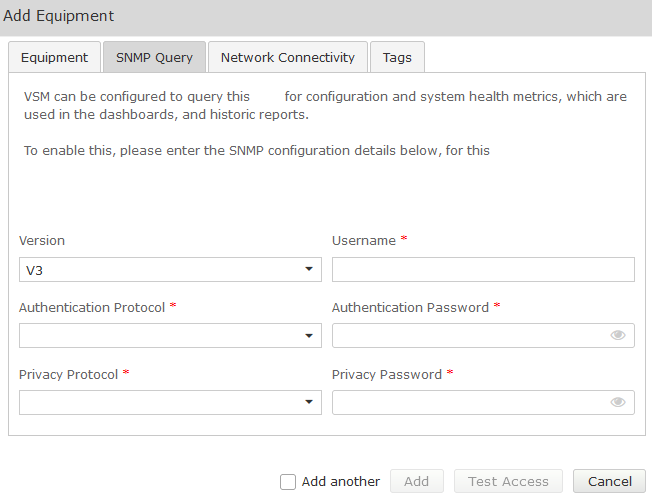
SNMP V3
| Fields | Setting |
|---|---|
Version | V3 |
Username | SNMP V3 Username (refer to technical requirements forms) |
Authentication Protocol | SHA (Recommended) |
Authentication Password | Password (refer to technical requirements) |
Privacy Protocol | DES (Recommended) |
Privacy Password | Password (refer to technical requirements forms) |
Network Connectivity
Network connectivity settings are configured at the location level and apply to all equipment by default. See here for more information.
The default location-level network connectivity settings (which are detailed in the link above) may be overridden for specific equipment using this tab.
| Setting | Description |
|---|---|
| Disable Network Connectivity Ping for Equipment | Select 'No' (this is the default) to send out ping tests. Select 'Yes' to disable ping tests from being sent out. |
| Ping Frequency (minutes) | Defines the amount of time (in minutes) between each ping test. |
| Raise an alarm when maximum ping exceeds (x) ms | Check this box and define a time (in milliseconds) to raise an alarm when the ping response time exceeds your set maximum time limit. |
| Raise an alarm when the average ping exceeds (x) ms | Check this box and define a time (in milliseconds) to raise an alarm when the ping response time exceeds your set average time limit. |
| Raise an alarm when packet loss exceeds (x) % | Check this box and define a percentage to raise an alarm when the packet loss of pings sent exceeds your set limit. |
You can define alarm raising conditions using all, none or a mixture of the above “Raise an alarm when” settings
Tagging
From the add equipment pop up you can create new tags, apply existing ones, or disassociate existing tags for a specific piece of equipment.
Essentially, this tab implements the functionality on the Manage Tags page but localizes any configuration to the equipment being configured.
See here for more information.
CDR Files
Complete the Equipment tab and then click on the ‘CDR’ tab. Select the ‘Enable Collection of CDR Files’ checkbox. Then fill out the fields using the table below.
This is only required if you are collecting CDR Files from Session Manager.
Web Portal – SM CDR Field Description
Field | Setting |
|---|---|
Enable Collection of CDR Files | Selected |
Delete CDR Files After Download | Recommended |
File Type | Flat |
SFTP User Name | The SFTP username you added to SM earlier |
SFTP Password | The SFTP password you added to SM earlier |
Test Access
Once all fields are populated Click on the 'Test Access' button. This will test that VSM can connect to the SM using the settings you have entered:
Both SSH and SNMP should return success. If not, troubleshoot the configuration.
- The SSH test ensures the VSM collector can connect to, and log in using the account configured.
- The SNMP test ensures an SNMP query can be run.
Once testing is successful, click Add.
Generate Test Alarm
Browse to System Manager and log in. Navigate to Services > Inventory from the dashboard. Navigate to Manage Serviceability Agents > Serviceability Agents:
Generate a Test Alarm by selecting the SM Agent, and clicking on the 'Generate Test Alarm' button.
Return to the VSM home page. For the particular customer, select Availability Manager > Manage Alarms:
The test should show as an alarm. If not, troubleshoot the configuration.
This test has the SM generate an SNMP trap and ensures VSM receives the same.
The SM configuration is now complete.